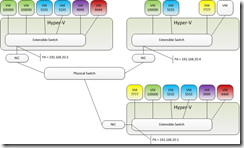
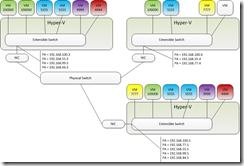
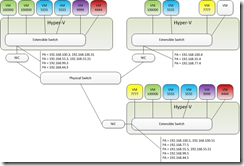
I am finally at the last part that makes this all work.
If you have defined everything so far you have VM traffic routing between VMs on the same Virtual Switch (and it is isolated like a tiny VLAN) but nothing more. No traffic will travel from VM to VM across hosts until we define the Lookup Route that tells that packet where to go.
here is the command in a nutshell:
New-NetVirtualizationLookupRecord -VirtualSubnetID 5001 -CustomerAddress 192.168.104.10 -MACAddress 00155D002001 -ProviderAddress 10.235.0.31 -Rule TranslationMethodNat -CustomerID "{2ad17590-33b5-45fc-ad3a-90e5ff9b017f}" -VMName VMPXE
The VirtualSubnetID, the CA (the IP of the VM), the MAC of the VM, the PA that the CA is associated with, the type of network virtualization to use, the Routing Domain (Customer ID) and the name of the VM (really for management benefits – it does not have to match anything).
The –Rules are TranslationMethodNat (for IP Rewrite) or TranslationMethodEncap for (NVGRE encapsulation). This is that decision I mentioned before.
If your traffic is all IP based and can handle segmentation then by all means use encapsulation (also, your physical devises must support it, most do, but as long as they don’t somehow do something with the virtual subnet ID you should be good).
Otherwise fall back to Nat (IP Rewrite). But, remember that if you use this you need one PA for each CA, so you need to add PA addresses each time you add a VM. And don’t worry, you can define multiples on the physical NIC of the virtual switch.
Here I have a script to set up encapsulation on a static network (where I don’t have to worry about VM change).
Here are my assumptions:
- The PA is defined and I am using one for all VMs
- The VMs are running and reporting an IP address to Hyper-V
- I write an output file to run on the ‘other’ Hyper-V Servers to propagate the Lookup Routes.
- If the IP is 0.0.0.0 I ignore it.
There is a lot going on here and the screen does not format it well, be warned.
$paAddress = Get-NetVirtualizationProviderAddress
$otherHostsFile = $env:Public + "\Documents\" + "RunOnHostsOtherThan_" + $env:COMPUTERNAME + ".ps1"
Out-File -Force $otherHostsFile # this is the propagation file$vms = Get-VM -Name *
foreach ($i in $vms) {
$i.VMNameif ($i.NetworkAdapters.IPAddresses -ne $null) {
$vmIpv4 = $i.NetworkAdapters.IPAddresses | where { $_.contains(".") }
$vmIpv6 = $i.NetworkAdapters.IPAddresses | where { $_.contains(":") }
}
$vmNic = Get-VMNetworkAdapter -VM $i" " + $vmNic.Name + " -> " + $vmNic.SwitchName
if ($vmIpv4 -ne $NULL) {
New-NetVirtualizationLookupRecord -VirtualSubnetID $vSubnetId -CustomerAddress $vmIpv4 -MACAddress $vmNic.MACAddress -ProviderAddress $paAddress.ProviderAddress -Rule TranslationMethodEncap -CustomerID $routingDomainId -VMName $vmNic.VMName
Set-VMNetworkAdapter -VirtualSubnetId $vSubnetId -VMNetworkAdapter $vmNic
("New-NetVirtualizationLookupRecord -VirtualSubnetID " + $vSubnetId + " -CustomerAddress " + $vmIpv4 + " -MACAddress " + $vmNic.MACAddress + " -ProviderAddress " + $paAddress.ProviderAddress+ " -Rule TranslationMethodEncap -CustomerID `"" + $routingDomainId + "`" -VMName " + $vmNic.VMName) | Out-File -NoClobber -Append -FilePath $otherHostsFile}
<# If ($vmIpv6 -ne $NULL) {
New-NetVirtualizationLookupRecord -VirtualSubnetID $vSubnetId -CustomerAddress $vmIpv6 -MACAddress $vmNic.MACAddress -ProviderAddress $paAddress.ProviderAddress -Rule TranslationMethodEncap -CustomerID $routingDomainId -VMName $vmNic.VMName
Set-VMNetworkAdapter -VirtualSubnetId $vSubnetId -VMNetworkAdapter $vmNic
("New-NetVirtualizationLookupRecord -VirtualSubnetID " + $vSubnetId + " -CustomerAddress " + $vmIpv6+ " -MACAddress " + $vmNic.MACAddress + " -ProviderAddress " + $paAddress.ProviderAddress+ " -Rule TranslationMethodEncap -CustomerID `"" + $routingDomainId + "`" -VMName " + $vmNic.VMName) | Out-File -NoClobber -Append -FilePath $otherHostsFile
}#>Clear-Variable -name vmIpv4 -ErrorAction SilentlyContinue
Clear-Variable -Name vmIpv6 -ErrorAction SilentlyContinue
}
I have another script to set up NAT and that takes a bit more due to the PA management. A post of its own.